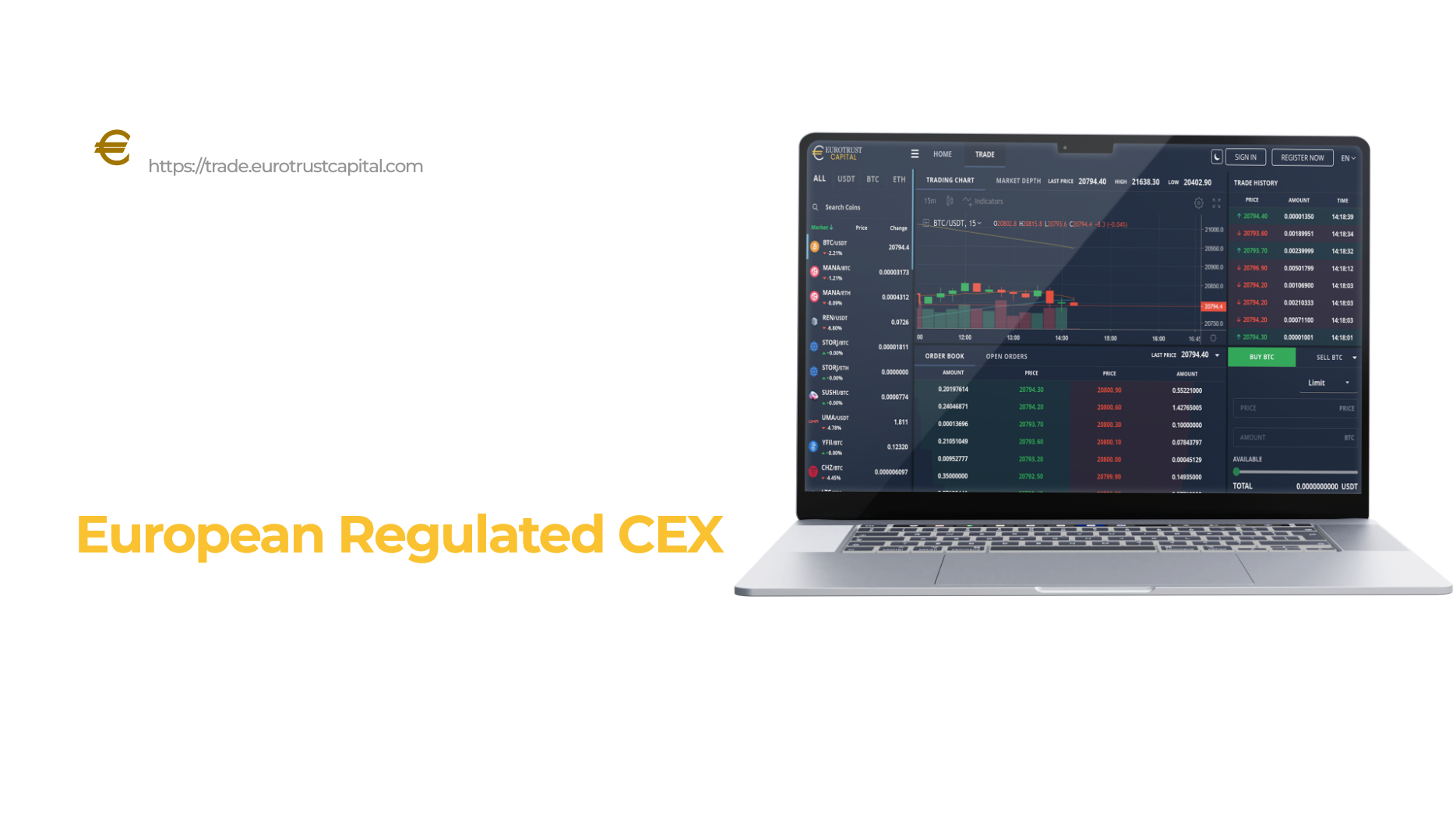
Crypto Web & Mobile Mining Solution
Our cutting-edge crypto web and mobile mining solution, designed to empower your users with the ability to mine cryptocurrencies using their own mining rigs, PCs, and mobile devices. By harnessing the combined power of these resources, our platform offers the potential to generate substantial crypto rewards for your users. Get ready to tap into the world of crypto mining and unlock incredible opportunities for your community.
How Crypto Web & Mobile Miner Works?
Our Crypto Web & Mobile Miner provides a user-friendly platform for mining cryptocurrencies using web browsers and mobile devices. Upon registration, users can choose their preferred mining option and contribute their device's processing power to a mining pool. The platform utilizes various mining algorithms to optimize performance and profitability.
As mining pool successfully mines new blocks and validates transactions, rewards are distributed proportionally among participants based on their contributed mining power. Users can monitor their mining progress and earnings through a user-friendly dashboard in real-time. Once a specific threshold is reached, users can easily withdraw their earned cryptocurrencies to their wallets, making it a convenient and accessible solution for cryptocurrency mining without the need for specialized equipment.
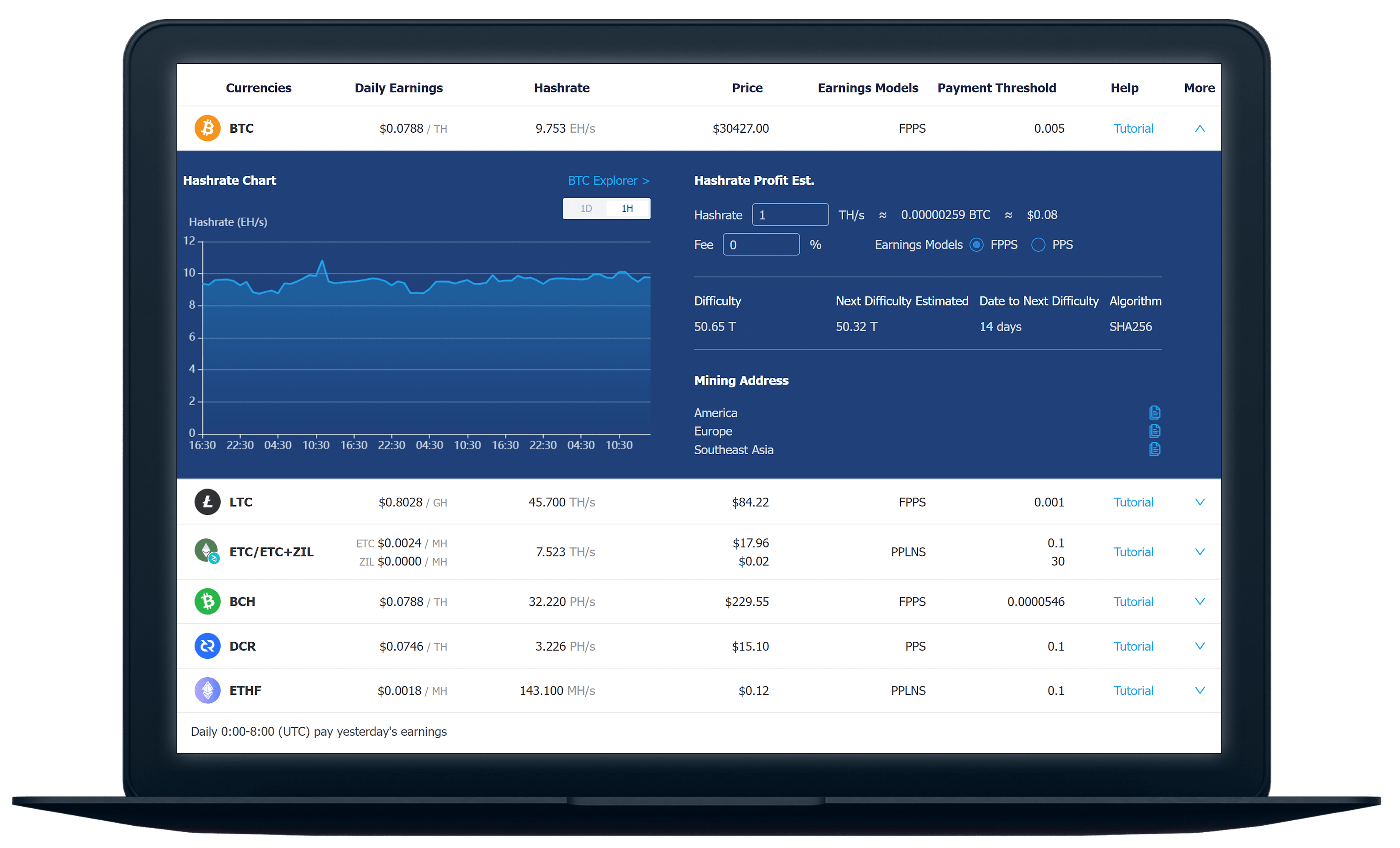
The Solution SaaS
Our Crypto Web & Mobile Mining Solution opens up a world of possibilities for your users to earn block rewards across multiple blockchains. Whether they choose to rent hashing power or combine their existing resources, our platform enables them to actively engage in the lucrative process of cryptocurrency mining. By tapping into this innovative solution, users can take advantage of the dynamic crypto landscape and unlock the potential for substantial earnings.

Discover the power of our Crypto Web & Mobile Mining Solution, boasting an impressive hashrate that ensures efficient mining of numerous cryptocurrencies. Whether using web browsers or mobile devices, users can tap into this cutting-edge platform to unlock the potential for substantial rewards. With its strong hashrate capabilities, our solution maximizes mining efficiency, making it a highly profitable option for cryptocurrency enthusiasts.



Introducing an innovative security feature that adds an extra layer of protection to the mining operations, safeguarding the hashrate from potential attacks and ensuring a stable mining experience for all users. With this robust security measure in place, users can have peace of mind, knowing that their mining activities are shielded from any malicious attempts, allowing them to mine cryptocurrencies with confidence and uninterrupted efficiency.

Our Crypto Web & Mobile Mining Solution opens up a world of possibilities for your users to earn block rewards across multiple blockchains. Whether they choose to rent hashing power or combine their existing resources, our platform enables them to actively engage in the lucrative process of cryptocurrency mining. By tapping into this innovative solution, users can take advantage of the dynamic crypto landscape and unlock the potential for substantial earnings.

Discover the power of our Crypto Web & Mobile Mining Solution, boasting an impressive hashrate that ensures efficient mining of numerous cryptocurrencies. Whether using web browsers or mobile devices, users can tap into this cutting-edge platform to unlock the potential for substantial rewards. With its strong hashrate capabilities, our solution maximizes mining efficiency, making it a highly profitable option for cryptocurrency enthusiasts.

Introducing an innovative security feature that adds an extra layer of protection to the mining operations, safeguarding the hashrate from potential attacks and ensuring a stable mining experience for all users. With this robust security measure in place, users can have peace of mind, knowing that their mining activities are shielded from any malicious attempts, allowing them to mine cryptocurrencies with confidence and uninterrupted efficiency.
Benefits of Crypto Web & Mobile Mining Solution
Our Crypto Web & Mobile Mining Solution offers accessibility and convenience, allowing users to mine cryptocurrencies using their web browsers and mobile devices without the need for specialized hardware. With optimized performance, real-time monitoring, and secure operations, users can join mining pools, maximize earnings, and easily withdraw rewards. Whether you're a seasoned miner or new to the world of cryptocurrencies, our platform provides a cost-efficient and user-friendly way to explore and benefit from the dynamic crypto landscape.

Rewards
Rewards the volume of visitors, not the number of ads you show.

Strategy
Can work in conjunction with your current monetization strategy.

Increase Revenue
Improve your user experience by not increasings ads to increase revenue.

Loyalty Reward
Allows you to reward your visitors, gamers, or app users to build loyalty.

Full Transparency
Full transparency to all your users, nothing is hidden.

Monthly Payouts
Monthly payouts options in fiat, not a volatile crypto currency.
Web & Mobile Miner Key Highlights

Informative Dashboard
Experience the convenience of our easy-to-use and efficient dashboard, providing quick access to essential information. With its user-friendly interface, you can effortlessly initiate your mining operations with just a few simple clicks. Enjoy a seamless and straightforward mining experience, all within your control at your fingertips.

Device Monitoring
Take full control of every device in your system with our platform. Monitor crucial details like temperature, load, fan speed, and profits conveniently from one centralized place. Enjoy the ease of managing all your devices and mining operations effortlessly, ensuring a smooth and informed mining experience.

Benchmark
Utilize accurate benchmarking to assess the most profitable algorithms for your hardware, or personally select the preferred algorithms you wish to support. With our platform, you have the flexibility to make informed choices and optimize your mining performance according to your preferences and hardware capabilities.

Plugins
Elevate your mining experience by integrating third-party miners through our plugins, transforming our platform into an advanced and cutting-edge mining solution. With the flexibility to incorporate external tools, you can customize and enhance your mining operations to suit your specific needs, unlocking even greater potential for profitability and efficiency.
Setting the Industry Standard for
Cutting-Edge Mining

Safe & Ad Free
Website visitors have a strong aversion to ads, with nearly all users finding them intrusive. Many individuals also view targeted ads as a violation of their privacy, further contributing to their dislike of advertising on websites.
AI Processing Power
New Monetization Method: Earn monthly revenue by leveraging users' compute power for AI processing. Maximize earnings through this cutting-edge solution and explore new possibilities for your business.
Easy to Go Live
Simplicity at its Finest: Get up and running with just a few lines of code. Our platform makes it incredibly easy to start and navigate. No complicated setup or technical expertise required.
Partners We Trust
Our mission is to pioneer cutting-edge products and solutions, setting a new industry standard for excellence. We prioritize collaborations that drive innovation and propel us forward in creating groundbreaking offerings.
Data Security
Backup of data in two modes
Two data backup modes are available: real-time replication and daily scheduled backup. Real-time replication instantly mirrors changes, providing continuous protection. On the other hand, the daily scheduled backup saves modified data at predetermined intervals, ensuring regular data preservation. Choose the mode that suits your needs best.
Authorization through
two-factor authentication
Exchange employs two-factor authentication to bolster the security of multiple admin panels. This process entails sending a secure link via email and requesting a token, providing an extra layer of protection against unauthorized access to the system. By requiring both the secure link and token, the system ensures enhanced authorization measures, safeguarding sensitive information and bolstering overall security.
IP-based access restrictions
IP-based access restrictions involve associating an IP address with a login password or key to control system access. In Exchange, for instance, the payment system can only be accessed from a pre-defined IP address, ensuring secure and limited access to authorized users. This mechanism adds an extra layer of protection, mitigating potential unauthorized access and enhancing overall security measures.
Database with encryption
Client personal information is stored in an encrypted database partition, ensuring that the data remains inaccessible even from the server itself. This encryption measure provides an additional layer of security, safeguarding sensitive information from unauthorized access and protecting the privacy of clients' data.
Replication of databases securely
Secure replication of databases is achieved through SSL-enabled database replication, effectively eliminating the risk of man-in-the-middle (MITM) attacks. By employing SSL encryption, the data transmission between the databases is protected from interception and unauthorized access, ensuring the integrity and confidentiality of the replicated data.
Access Security
Access logs
For auditing and security purposes, all database server accesses are logged, providing a comprehensive trail of actions, including details like timestamps, users, operations performed, and data involved. This meticulous logging ensures accountability, helps detect potential breaches, and ensures compliance with regulatory requirements and data governance practices.
External data exchange that is secure
To ensure secure external data exchange, a unique authentication key is used when interacting with external systems like payment systems. After each data exchange, the signature is verified to guarantee its authenticity and maintain a high level of data security and integrity throughout the process. This approach provides a robust and reliable method to safeguard sensitive information during external data transactions.
SSH Keys
SSH keys are employed by Ment Tech personnel for server access, with access limited to a select few individuals who use encrypted disks on their computers. This measure effectively mitigates data breach risks resulting from laptop theft, ensuring the utmost confidentiality of sensitive information. By combining SSH keys and encrypted disks, the company ensures robust security measures are in place to safeguard critical data from unauthorized access.
Document security
Document security is prioritized by not storing any client documents within our database. Instead, data processing takes place through a cloud-based solution offered by a third-party provider. For utmost protection, all client documents are securely stored by third-party KYC (Know Your Customer) providers, strictly adhering to the contract terms. This approach ensures the confidentiality and integrity of sensitive client information.
Change monitoring
Change monitoring is a crucial aspect of our security measures. We conduct continuous monitoring of critical data, including password hashes. In case of any alterations, immediate notifications are sent through two separate channels, ensuring real-time awareness and bolstering our security protocols. This proactive approach helps safeguard against potential security breaches and enhances overall data protection.
High-level DDoS mitigation is employed to secure our servers, preventing disruptive bad traffic while allowing good traffic to pass through smoothly, ensuring high availability and optimal performance of websites, applications, and APIs.
Dedicated Support Team
We are dedicated to providing support and taking responsibility when you need assistance, and will never pass the buck by saying it's not our issue. We maintain a comprehensive logging system for all comments and details from our developers across our entire product line, ensuring that we are able to assist you effectively without having to repeatedly ask for information.
Resources & Tutorials
Ment Tech places a strong emphasis on delivering exceptional user experience. This is achieved by partnering closely with clients and providing a wealth of tutorials and resources to assist with technical needs. The team is knowledgeable and dedicated to ensuring a seamless experience.
Instruction
At Ment Tech, education is a key part of our service offering. We strive to provide our clients with the knowledge and understanding they need to succeed, which is why we offer video training and demonstrations in addition to a wide range of tutorials and materials. Our goal is to ensure the ultimate user experience for our clients.
Dedicated Experts for Each Project
At Ment Tech, we take great pride in our commitment to excellence. With an unwavering dedication to delivering successful outcomes, we ensure that every project is handled by a team of dedicated experts. These professionals are carefully assigned based on their specialized skills and knowledge, ensuring that each endeavor receives the attention it deserves. Our emphasis on English language proficiency further ensures effective communication and understanding throughout the entire project lifecycle. Experience the difference of having expertly assigned teams working passionately to achieve your goals .

Project Manager
We provide each of our clients with a dedicated project manager, readily available to address inquiries and cater to their specific needs.

QA Engineer
All our projects are supported by a dedicated QA Engineer, ensuring meticulous testing and quality assurance to meet the highest standards of excellence.
DevOps Engineer
Our dedicated DevOps Engineer ensures seamless integration, continuous delivery, and efficient infrastructure management for successful project development.

UI & UX Engineer
Our UI/UX Engineer crafts intuitive designs and seamless interactions, delivering exceptional user experiences for your project.

Blockchain Engineer
The Blockchain Full-Stack Engineer develops innovative solutions, combining front-end and back-end expertise for execution.

Business Analyst
Our Business Analyst plays a crucial role in analyzing and interpreting data to inform effective business strategies, ensuring successful project outcomes.
Some of Our Exceptional Achievements
Interested in Working Together? Let's Talk!
We're interested in hearing your ideas and discussing them further. Before we proceed, we will send you a Non-Disclosure Agreement (NDA) to ensure the confidentiality of all information shared. Your privacy is of utmost importance to us.
- 2019 - 2025 © Ment Tech Labs Pvt. Ltd